Hello, hello! In this blog post, we’ll explore how to configure SSH keys in two different ways:
- Using the Azure Portal
- Using Azure CLI
Before we dive into the technical details, let’s quickly recap what SSH keys are and how they work.
What are SSH Keys?
SSH keys are a secure authentication method used to access remote systems, most commonly Linux-based virtual machines. They are part of the Secure Shell (SSH) protocol, which encrypts communication between a client and a server.
How SSH Keys Work
SSH keys operate using public-key cryptography, where a key pair is generated:
Private Key
Stored securely on your local machine. This key should never be shared.Public Key
Placed on the remote server (e.g., an Azure VM). This key allows access when a matching private key is used.
When you connect to a remote machine, SSH verifies that your private key matches the stored public key, granting access without requiring a password.
Why Use SSH Keys?
- Stronger security: More resistant to brute-force attacks than passwords.
- Convenience: No need to remember or type passwords for each login.
- Automation: Ideal for automated deployments and secure remote access in DevOps workflows.
SSH Key Generation Algorithms
When creating SSH keys using the ssh-keygen tool, you can choose from several cryptographic algorithms, each with different strengths and use cases. Below are some common algorithms you might encounter:
DSA (Digital Signature Algorithm)
- Strengths: Previously popular, but considered less secure than newer algorithms like RSA or ECDSA.
- Key Length: Typically 1024-bit keys (but it’s recommended to avoid DSA due to its security limitations).
- Use Case: Mostly deprecated due to security concerns.
To generate a DSA key:
| |
RSA (Rivest-Shamir-Adleman)
- Strengths: One of the most widely used and supported algorithms for SSH keys.
- Key Length: Typically uses 2048-bit or 4096-bit keys for better security.
- Use Case: Commonly used for both SSH access and securing other types of communication.
To generate an RSA key:
| |
ECDSA (Elliptic Curve Digital Signature Algorithm)
- Strengths: Offers higher security with shorter key lengths compared to RSA. Uses elliptic curve cryptography (ECC), which is more efficient.
- Key Length: Common key lengths are 256-bit, 384-bit, and 521-bit.
- Use Case: Ideal for environments where performance and security are paramount, such as in cloud-based systems.
To generate an ECDSA key:
| |
Ed25519
- Strengths: Known for being extremely secure and fast, with a fixed 256-bit key length. It’s resistant to many known cryptographic attacks.
- Key Length: 256-bit (fixed length).
- Use Case: Recommended for modern SSH deployments, providing excellent performance and strong security.
To generate an Ed25519 key:
| |
Choosing the Right Algorithm
For Most Use Cases:
Ed25519 is recommended due to its strong security and efficiency.For Compatibility:
RSA is still widely supported, but it is slower and requires longer key sizes for equivalent security to Ed25519.For High Security:
ECDSA with a 521-bit key length offers excellent security and performance.
Best Practices for SSH Keys
✅ Use a strong passphrase to protect your private key.
✅ Restrict permissions (chmod 600 ~/.ssh/id_rsa) to prevent unauthorized access.
✅ Rotate SSH keys regularly to reduce security risks.
✅ Use an SSH agent (ssh-agent) for secure key management without storing passphrases in plain text.
✅ Disable password authentication to enforce key-based access on remote machines.
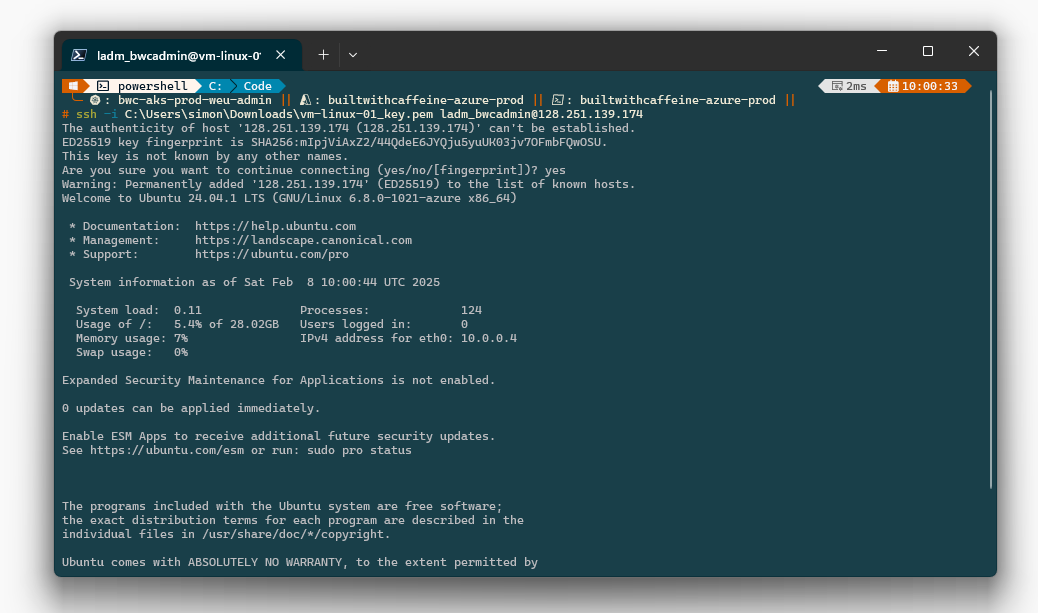
Azure Portal - New Linux Machine
When creating a new virtual machine from the Azure Portal, if you wish to use SSH Keys over a traditional password, when creating the machine under the Basic tab you will want to change the authentication type.
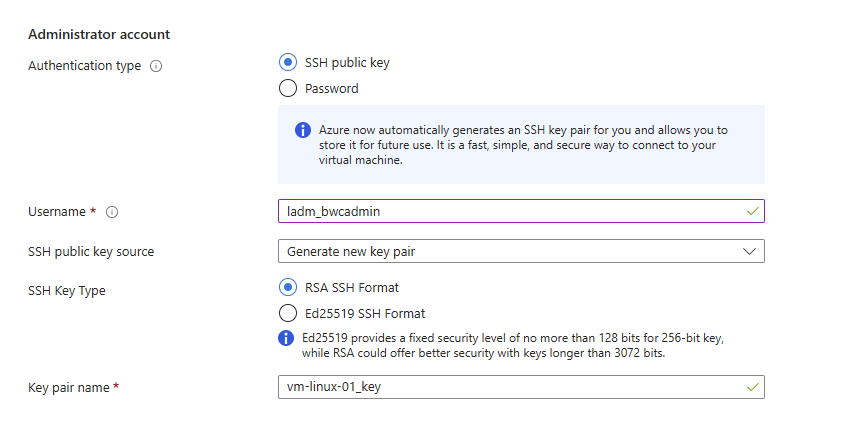
Once you have created the machine you will see an extra prompt giving you the Private key for the sshley pair.
Important 🚨
When deploying a virtual machine with SSH keys, password authentication is automatically disabled.
This setting is permanent for the VM. If you need to enable password authentication later, you must redeploy the VM from an image.
| |
Azure Portal - Adding SSH Keys
In this scenario we have an existing machine which has been deployed and we want to look at adding sshkeys to a user on the machine.
From the Virtual Machine overview, head to Reset Password
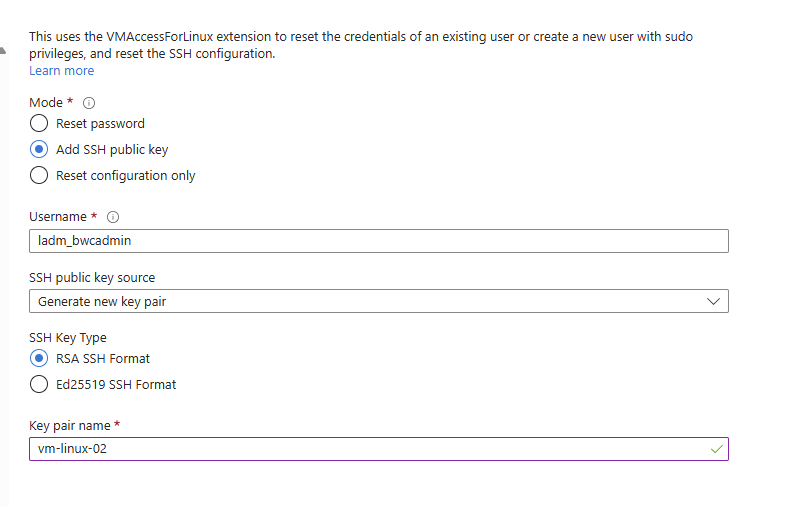
Once you create/update the sshkey pair, you will be prompted to download the private key.
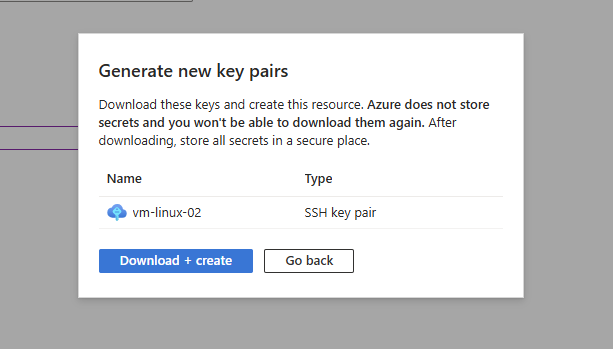
Tip
When managing SSHKeys the public key is stored under:
/home/username/.ssh/authorized_keys
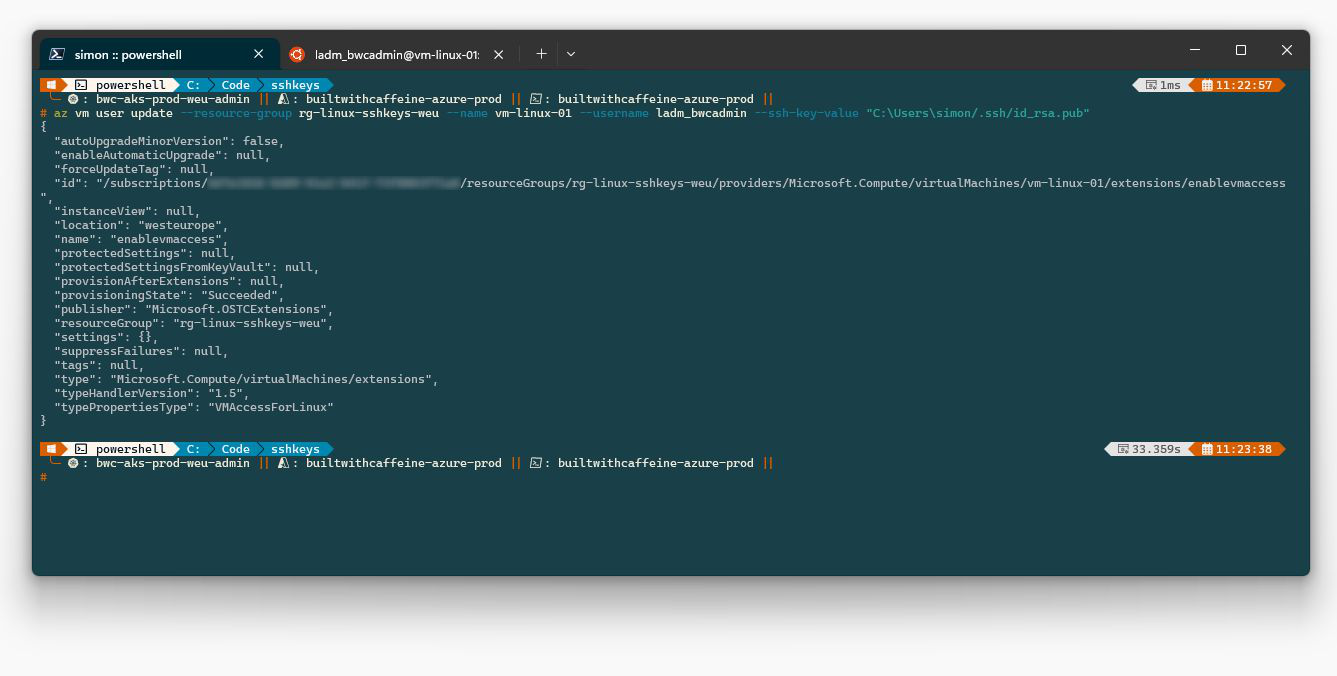
Azure CLI - Adding SSH Keys
Firstly we need to create a new sshkey pair
| |
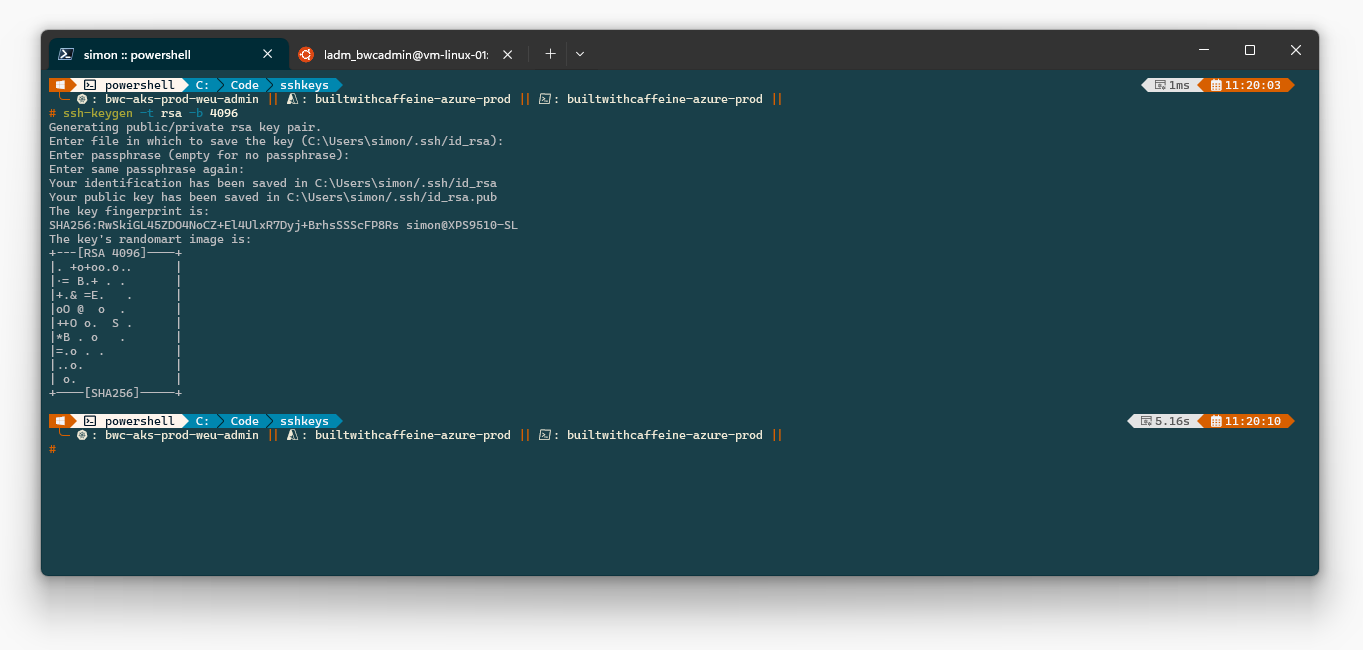
Tip
—ssh-key-value <- this needs to be the public key.
For Example: C:\Users\simon/.ssh/id_rsa.pub
| |
Connecting to Virtual Machine
Windows
| |
Security Tip
When using linux, to make the pem key more secure you can use:
chmod 600 vm-linux-01_key.pem
4 -rw——- 1 lnxuser lnxuser 2459 Feb 8 10:03 vm-linux-01_key.pem
Linux
| |