Introduction
Managing SSH access to Linux virtual machines (VMs) in Azure can be challenging, especially in enterprise environments where traditional methods like SSH keys and passwords become difficult to scale. Key rotation, user onboarding/offboarding, and ensuring secure access across multiple VMs often lead to operational overhead and security risks.
Microsoft Entra ID (formerly Azure Active Directory) provides a centralized authentication solution, eliminating the need for local user accounts and key management. By integrating Entra ID with Azure RBAC (Role-Based Access Control), organizations can streamline SSH access management, improve security, and enforce least-privilege access with minimal administrative effort.
In this guide, we’ll walk through configuring Entra ID authentication for Linux VMs in Azure, covering role assignments, infrastructure automation using Bicep, and best practices for securing access.
For more information about Entra Id and Linux Auth options you can check the Microsoft Docs: here
Why Use Entra ID Authentication?
| Authentication Method | Pros | Cons |
|---|---|---|
| Username & Password | Simple to use, familiar to most users | Susceptible to brute force attacks, harder to manage at scale |
| SSH Keys | More secure than passwords, widely supported | Key distribution and rotation can be complex |
| Entra ID Authentication | Centralized access management, integrates with RBAC, eliminates direct credential handling | Requires additional configuration, depends on Entra ID availability |
For large organizations, Entra ID authentication is the recommended approach because it streamlines user management, enforces security policies, and integrates seamlessly with Azure’s RBAC model.
Configuring RBAC for Entra ID SSH
To enable Entra ID authentication for Linux VMs, users need specific RBAC roles assigned within Azure. The key roles include:
Virtual Machine Administrator Login:
1c0163c0-47e6-4577-8991-ea5c82e286e4
Grants SSH access with sudo privileges.Virtual Machine User Login:
fb879df8-f326-4884-b1cf-06f3ad86be52
Grants SSH access without sudo privileges.
Best Practice Configuration
Instead of assigning roles directly to users, the best practice is to use an Entra ID security group. This ensures that access is easily managed as team members join or leave.
Steps to configure RBAC using an Entra ID security group:
- Create an Entra ID security group
| |
Add relevant users to the group
Assign the appropriate role to the group at the subscription, resource group, or VM level
| |
Infrastructure As Code
For a structured deployment, we use Bicep modules to provision an Ubuntu 24.04 VM with Entra ID authentication enabled. You can check out all the code base over in the BWC Bicep Repository
Bicep Custom Module Required!
If you wish to deploy this solution using IaC, You need to create this local custom module.
This is the Azure AD based SSH Login
NOTE: For this Module, You need to configure a System Assigned Identity on the Machine
If you’re wanting to use the below Infrastructure As Code, Please create a folder structure as follows:
.\modules\compute\virtual-machines\extensions
and save the file as:
azureADSSHExtension.bicep
| |
Invoke-AzDeployment
| |
Infrastructure As Code
| |
When you are ready to execute the deployment you can use the following PowerShell:
| |
Authentication
Bastion
From the Connect Page of the Virtual Machine from the dropdown you will see a list of options
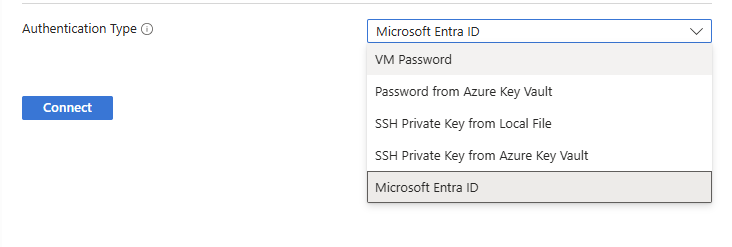
NOTE
If you have Virtual Machine Administrator Login or Virtual Machine User Login the option will auto update to Microsoft Entra Id
Click Connect and you will be logged in with your Entra Id User Account
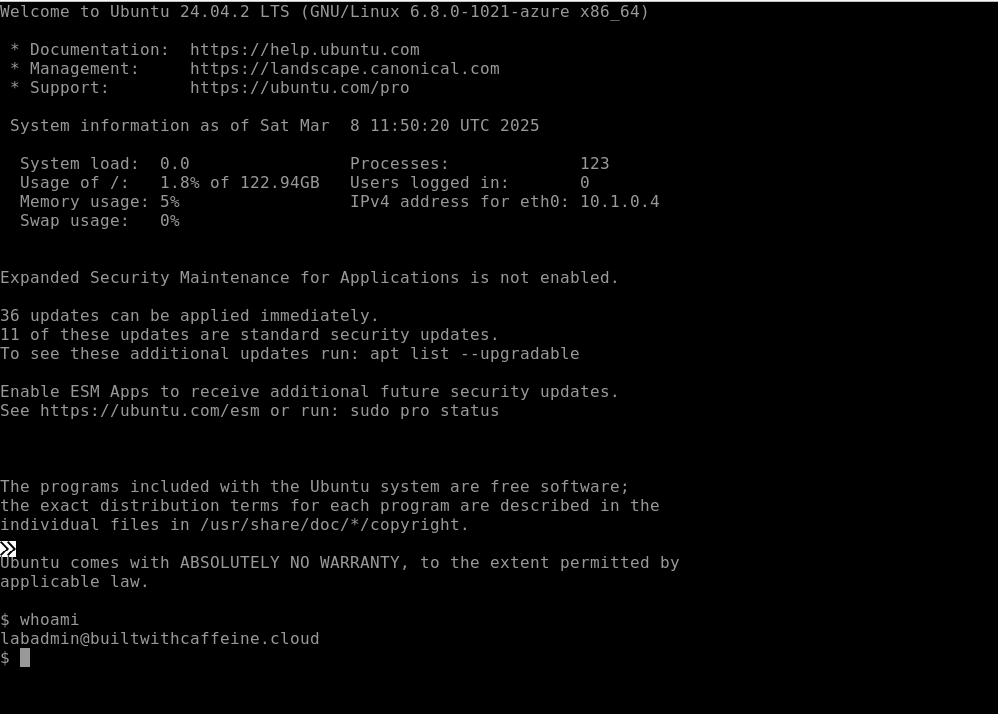
SSH Authentication
Using SSH Authentication from a terminal session or Cloud Shell, You can use the following commands
If you’re conencting using the Public IP address:
NOTE
Ensure you create an Inbound Security Rule in your Network Security Group (NSG) to allow TCP traffic on port 22 from your specific source IP or network. For enhanced security, restrict the source to your trusted IP range rather than allowing all traffic
| |
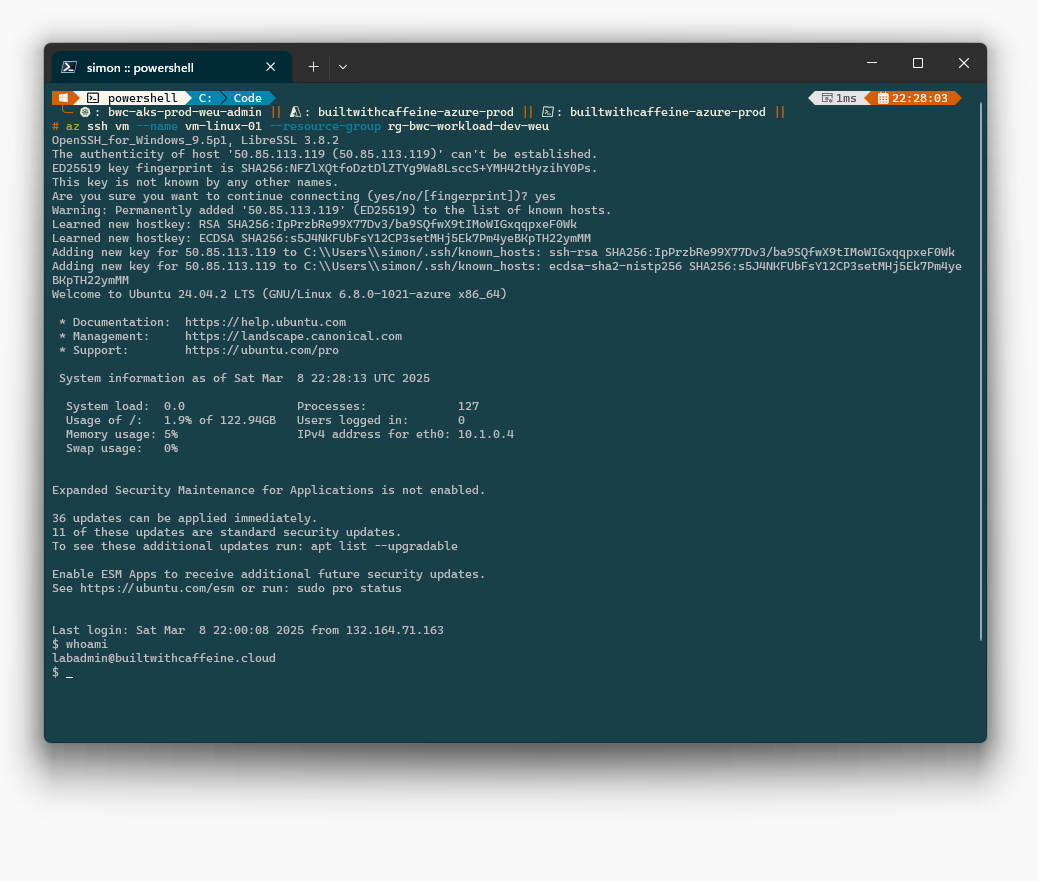
If you have a S/P2S connection, can can use the private IP address:
| |
Wrapping Up
Entra ID authentication for Linux VMs in Azure offers a seamless, secure, and scalable way to manage access. By integrating with Azure’s RBAC model, it eliminates the need for local account provisioning, enhances security by reducing credential sprawl, and simplifies management across multiple VMs.
For organizations running Linux workloads in Azure, adopting Entra ID authentication is a best practice that strengthens security, streamlines operations, and minimizes credential management overhead.
Next Steps
This post concludes our mini-series on Linux authentication options in Azure. If you’re exploring other authentication methods, check out the previous posts:
- Azure SSH Authentication for Linux
- Configuring SSH Keys on Azure Linux VMs
- Troubleshooting Missing SSH Keys in Azure
- Using Azure Bastion and Key Vault for Secure Access
To dive deeper, visit the official Microsoft documentation on Entra ID authentication for Linux VMs.
If you found this series helpful, feel free to share your thoughts or experiences in the comments!