What is Azure Bastion?
Azure Bastion is a fully managed service that provides secure and seamless RDP/SSH connectivity to virtual machines directly through the Azure portal, without requiring public IP addresses. By eliminating direct exposure to the internet, Azure Bastion significantly enhances security by reducing the attack surface and preventing common threats like brute-force attacks.
Why Use Azure Bastion?
Using Azure Bastion for SSH access to Linux VMs offers several advantages:
- Eliminates Public IPs: No need to expose SSH ports to the internet.
- Integrated Azure Portal Access: Securely connect to VMs via the Azure portal.
- No Client Software Needed: SSH directly from your browser without additional software.
- Enhanced Security: Supports Azure policies and private networking.
Azure Bastion SKUs
Azure Bastion comes in four SKUs, each offering different capabilities:
For more details, Check the official Microsoft Learn Docs: Bastion Overview Skus
| Feature | Developer SKU | Basic SKU | Standard SKU | Premium SKU |
|---|---|---|---|---|
| Connect to target VMs in same virtual network | Yes | Yes | Yes | Yes |
| Connect to target VMs in peered virtual networks | No | Yes | Yes | Yes |
| Support for concurrent connections | No | Yes | Yes | Yes |
| Access Linux VM Private Keys in Azure Key Vault (AKV) | Yes | Yes | Yes | Yes |
| Connect to Linux VM using SSH | Yes | Yes | Yes | Yes |
| Connect to Windows VM using RDP | Yes | Yes | Yes | Yes |
| Connect to Linux VM using RDP | No | No | Yes | Yes |
| Connect to Windows VM using SSH | No | No | Yes | Yes |
| Specify custom inbound port | No | No | Yes | Yes |
| Connect to VMs using Azure CLI | No | No | Yes | Yes |
| Host scaling | No | No | Yes | Yes |
| Upload or download files | No | No | Yes | Yes |
| Kerberos authentication | No | Yes | Yes | Yes |
| Shareable link | No | No | Yes | Yes |
| Connect to VMs via IP address | No | No | Yes | Yes |
| VM audio output | Yes | Yes | Yes | Yes |
| Disable copy/paste (web-based clients) | No | No | Yes | Yes |
| Session recording | No | No | No | Yes |
| Private-only deployment | No | No | No | Yes |
Bastion Pricing
For more details, Check the official Microsoft Docs: Bastion Pricing
| Bastion Sku | Cost Per Hour | Cost Per Month (730) |
|---|---|---|
| Developers | Free | Free |
| Basic | $0.19 | $138 |
| Standard | $0.29 | $211 |
| Premium | $0.45 | $328 |
Additional Bastion Unit Pricing
| Bastion Sku | Cost Per Hour | Cost Per Month (730) |
|---|---|---|
| Standard * | $0.14 | $102 |
| Premium * | $0.22 | $160 |
* Azure Bastion Standard and Azure Bastion Premium start with 2 instances as part of base pricing.
Bastion Out Bound Traffic Pricing
| Data Transfer | Pricing |
|---|---|
| First 5GB/Month | Free |
| 5Gb - 10TB/Month | $0.087 per GB |
| Next 40TB (10Tb - 50TB)/Month | $0.083 per GB |
| Next 100TB (50-150TB)/Month | $0.07 per GB |
| Over 150TB/Month | Contact Microsoft Support |
Why Store SSH Credentials in Key Vault?
Storing SSH keys in Key Vault enhances security by managing and protecting sensitive credentials in a central, secure location. Benefits include:
- Controlled Access: Use RBAC to restrict who can access SSH keys.
- Automated Secrets Rotation: Regularly update credentials without manual intervention.
- Integration with Azure Services: Use Key Vault with Azure Bastion for seamless authentication.
- Auditing & Monitoring: Track access and usage of stored credentials.
Infrastructure As Code Deployment
To ensure a repeatable and consistent deployment, we use Infrastructure as Code (IaC). Below is a placeholder for deploying Azure Bastion, Key Vault, and associated resources using Bicep.
Invoke-AzDeployment
| |
Infrastructure As Code
| |
Deployment Note
Please ensure Azure CLI and Bicep are installed.
AzCLI: winget install --exact --id Microsoft.AzureCLI
AzCLI Bicep: az bicep upgrade
Once you’ve saved the files locally you can execute the deployment using the following command:
| |
Resource Deployment
| Resource Group: Hub |
|---|
| Virtual Network |
| Bastion Host |
| Bastion Public IP |
| Resource Group: Spoke |
|---|
| Virtual Network |
| Key Vault |
| Log Analytics |
| Data Collection Rule |
| Network Security Group |
| Virtual Machine |
| Virtual Disk (OS) |
| Network Interface |
| Public IP Address |
Private Key Upload Notes
During the deploynent, We utilise ssh-keygen to generate the key value pair, using RSA and a key legnth of 2048.
| |
This will create the key value pair as:
azure-ssh-key.pub(Public Key)azure-ssh-key(Private Key)
The Public Key, will be passed into the Virtual Machine during the creation
Lines 316 - 321
| |
If you wanted to manually update the key at a later date, you can use the following Azure CLI Command, and for the Public Key, I recently wrote a post on how you can update the Public Key using the RunShellScript Lost SSH Keys
| |
Key Vault Role Based Access Control
During the deployment, The Azure CLI User will be given Key Vault Secret Officer.
If you require Read Only Access to the secrets you can use:
Key Vaylt Secret User: 4633458b-17de-408a-b874-0445c86b69e6
If you require Read/Write Access to the secrets you can use:
Key Vault Secret Officer: b86a8fe4-44ce-4948-aee5-eccb2c155cd7
Accessing the Machine via Azure Portal
Deployment Note
For this example default user is: azureuser
During the deploying of the Infrastcture, the Private Key is Uploaded into the Key Vault.
Once the deployment has completed, head to the resource group: 'rg-x-${customerName}-workload-${environmentType}-${locationShortCode}'
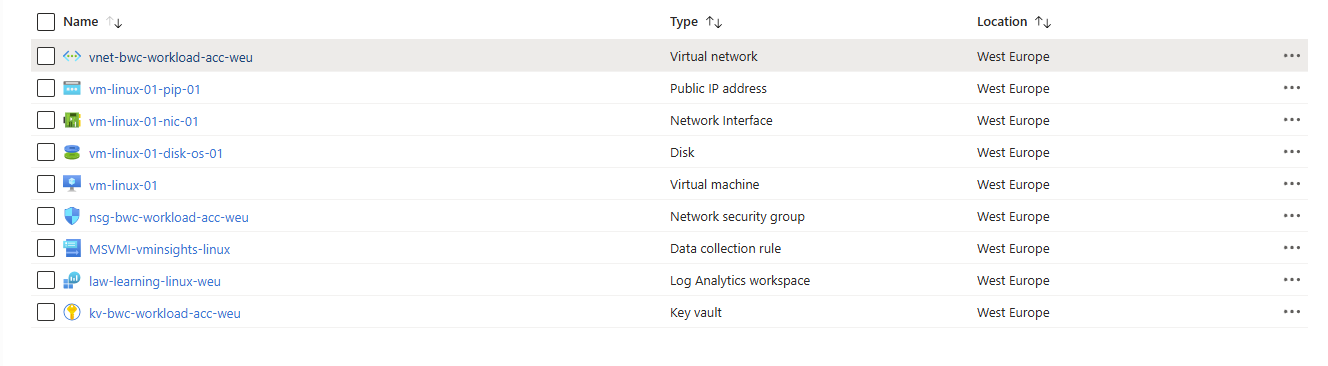
From the Virtual Machine Menu Blade, Under Connect choose Bastion
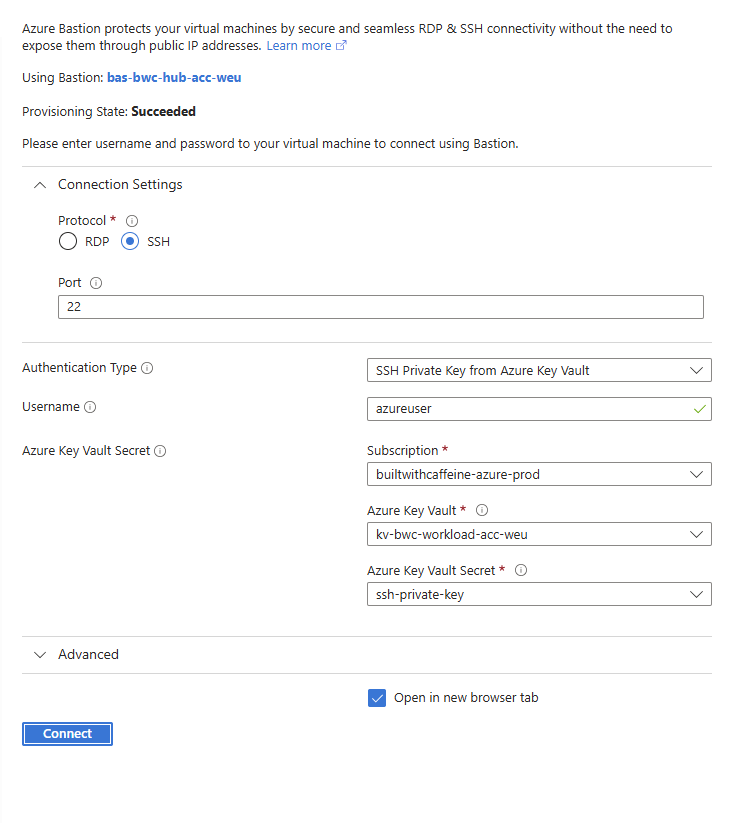
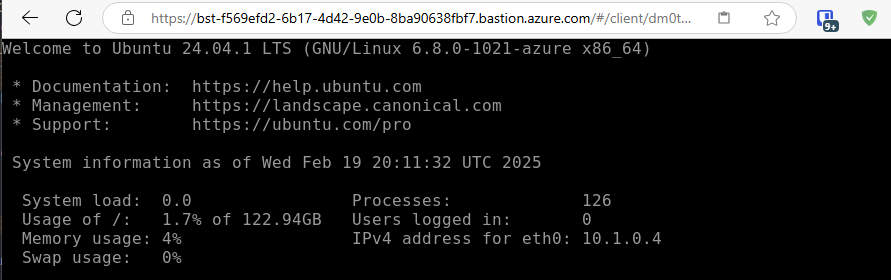
If everything has worked, you should get a sucessful authentication and find yourself connected to a Ubuntu Machine,
Wrap Up
Azure Bastion simplifies and secures SSH access to Linux VMs by eliminating public exposure. When combined with Azure Key Vault, it further enhances security by centrally managing and protecting SSH credentials. Leveraging Infrastructure as Code (IaC) ensures consistent, scalable, and repeatable deployments, making your cloud environment more robust and secure.