Keep it Secret, Keep it Safe 🧙♂️
Hello! Welcome to the fourth part of the Learning Git and GitHub series. In this post we will be covering how to keep your secrets safe when working with Git and GitHub. Committing secrets to a repository can be a big security risk, and in this post we will be covering how to avoid this!
What are secrets?
Secrets can be anything from API keys, passwords, or even connection strings. These are things that you do not want to be publicly available, and can be used to access sensitive information.
Why is this important?
When you commit secrets to a repository, they are available to anyone who has access to the repository. This can be a big security risk, and can lead to your data being compromised.
How can we avoid this?
There are a few ways that we can avoid committing secrets to a repository. One way is to use environment variables, and another way is to use a .gitignore file.
Using Environment Variables
Environment variables are variables that are set in the environment that your code is running in. These can be used to store secrets, and can be accessed by your code.
An example is using a .env file to store your secrets,
| |
| |
To call this into a script you can use the following,
| |
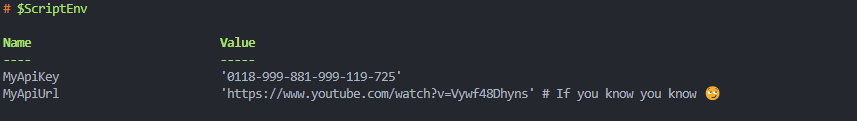
Don’t forget to add .env to your .gitignore file!
| |
Using GitHub Secret Scanning
GitHub has a feature called Secret Scanning, which scans your repository for secrets and alerts you if it finds any. This can be a useful tool to help you avoid committing secrets to your repository.
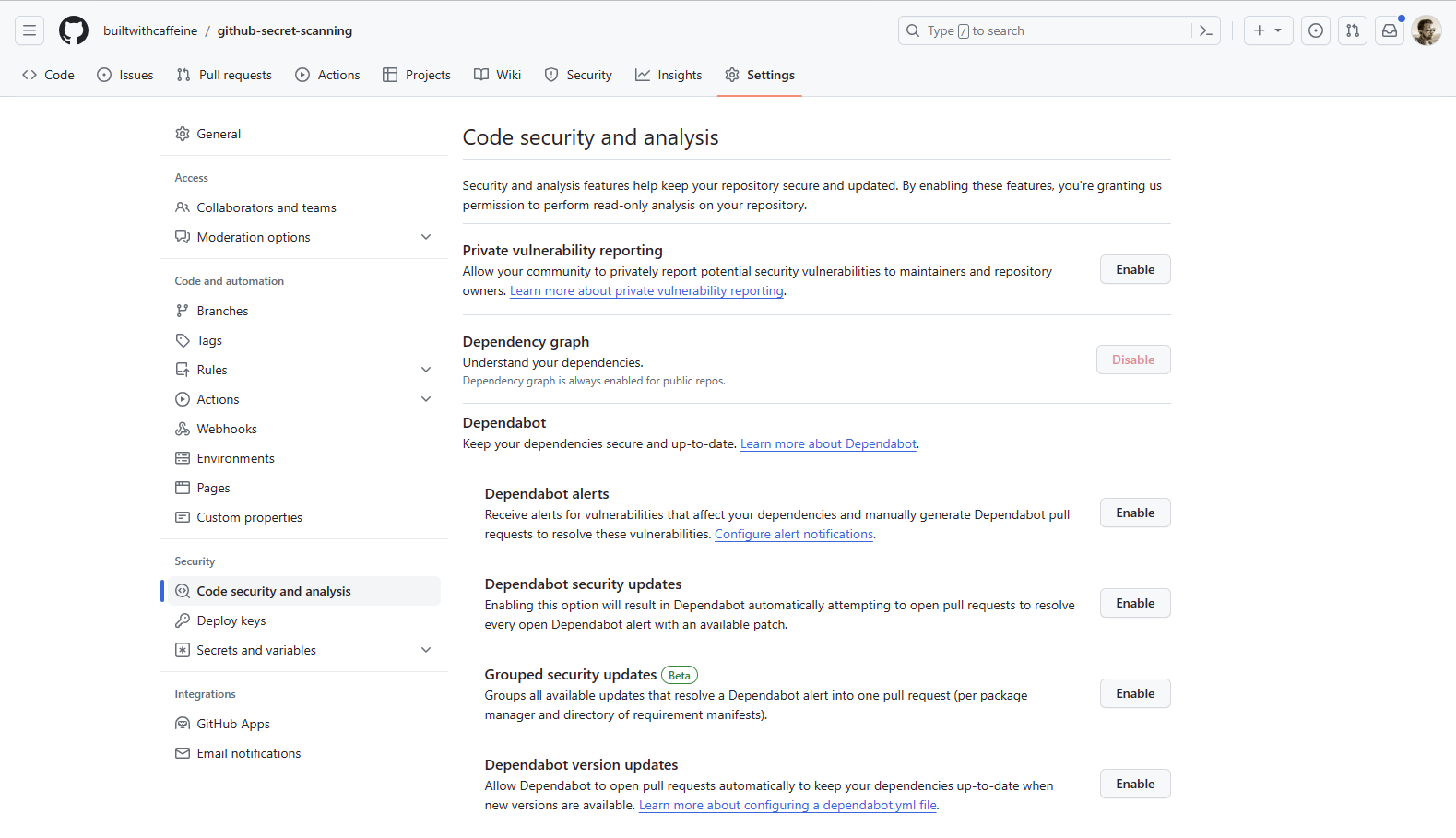
To enable Secret Scanning, go your repository settings, under Security click on Code security and analysis.
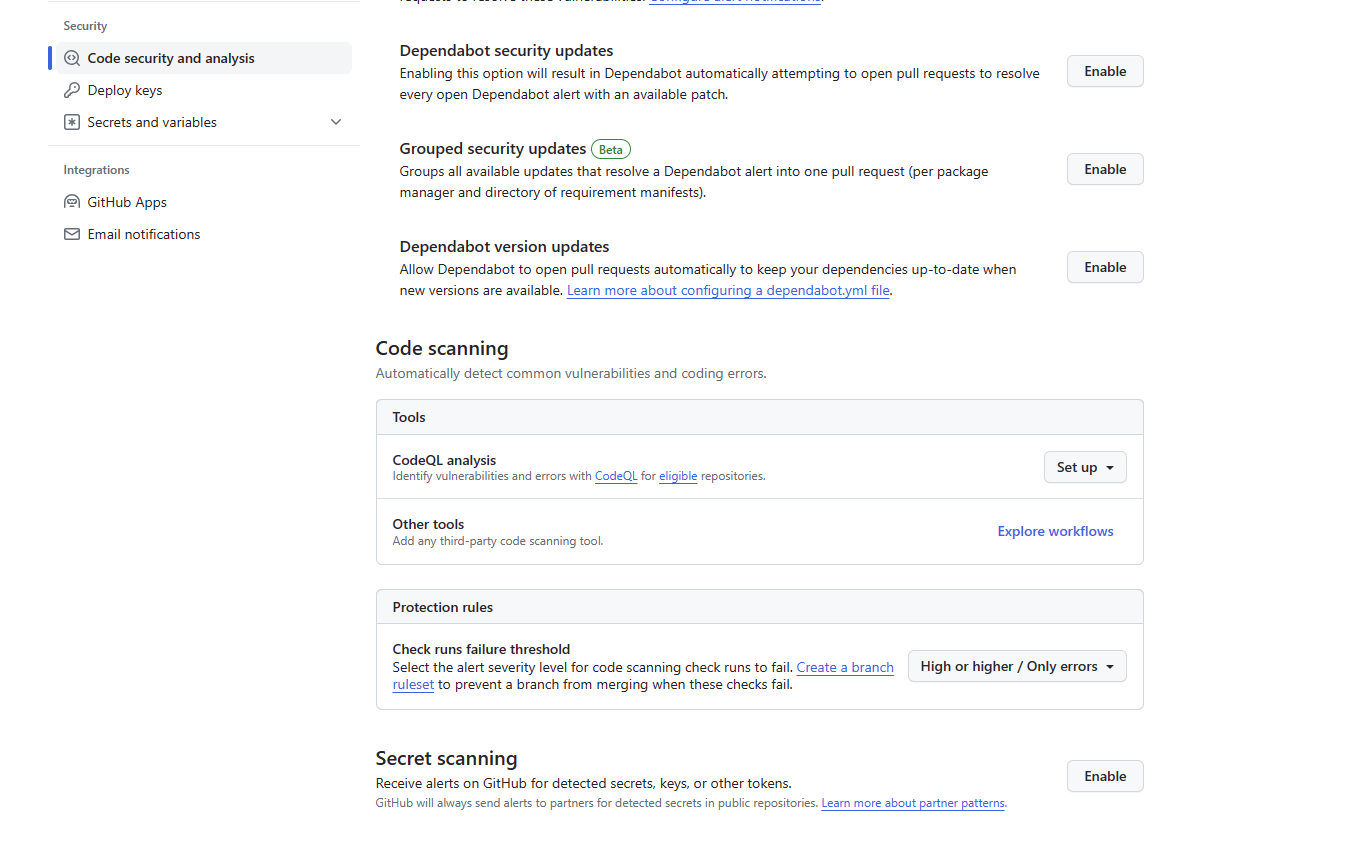
Enable secret scanning and push protection. If you want to learn more check out the GitHub documentation here.

Demo Time - Secret Scanning
Ok, so lets now test this out! - Because every one loves a demo! 🎉
For this scenario we have a repository called github-secret-scanning
For the test, we have a branch for feature/dev-deployment which has some powershell code in to create a service principal and then log into azure.
| |
Please note, these are bogus credentials and will not work.
Ok, So the mistake has been made and we have pushed the code to the repository. Lets see what happens!
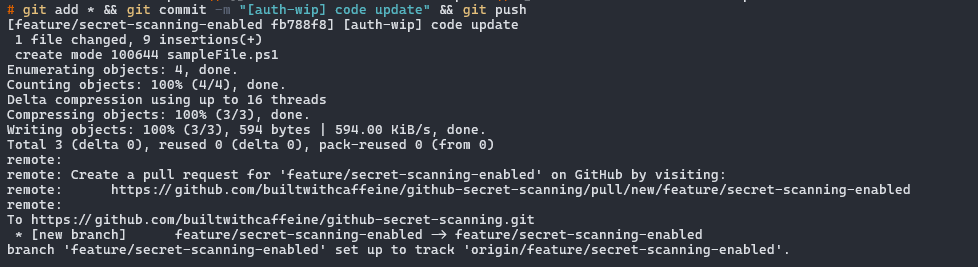
From the Github Repository, Under Security, Code scanning alerts, we can see that the secret scanning has found the secret in the code and has alerted us to it.
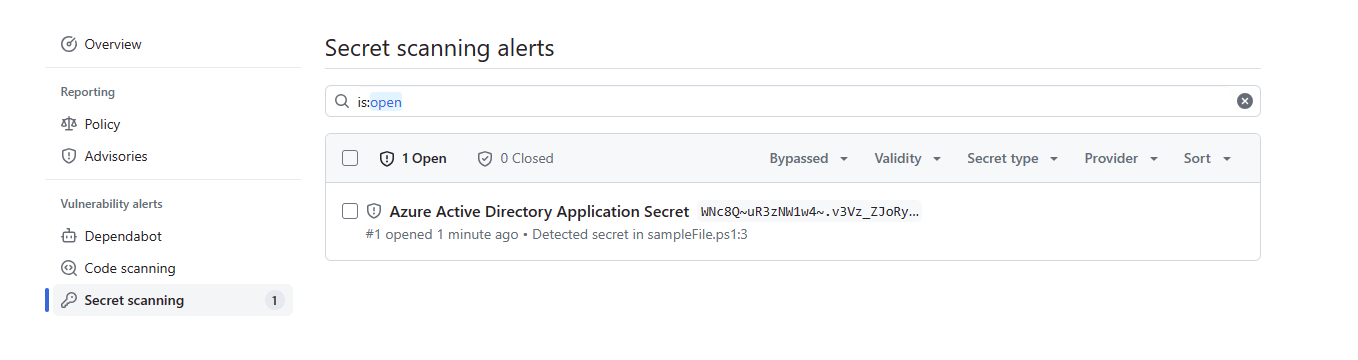
Drilling into the alert we can see the secret that has been found and the file that it is in.

Now, depending on the secret committed, you can either dismiss the alert, revoke the secret, mark as a false positive. In this case, we will fix the issue by removing the secret from the code and using environment variables instead.
Please note, that even if you remove the secret from the code, it will still be in the commit history. To remove it from the commit history, you will need to use the git filter-branch command.
Git Docs - Filter Branch
I should also add, that if this is with in an Organisation with the following roles will get alerts:
- Organization Administrators
- Repository Administrators
- Security Manager role
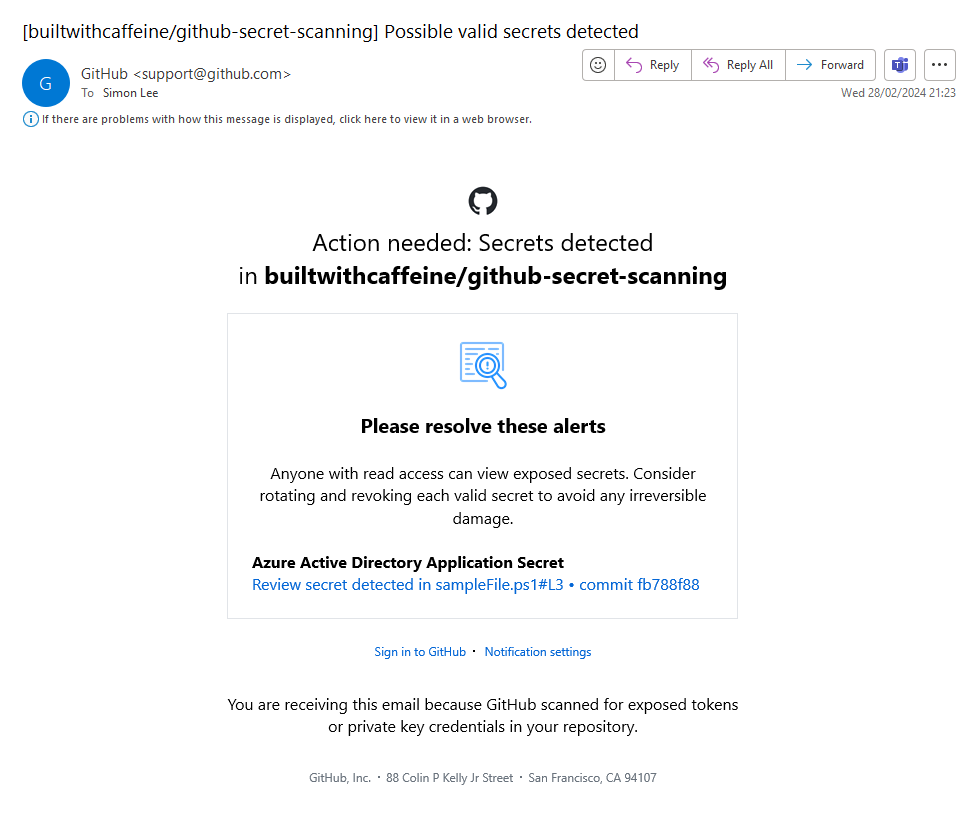
Demo Time - Push Protection
Ok, Now lets enable Push protection and Secret Scanning on the repository and see what happens when we try to push the secret to the repository. To do this we need to head back to the repository settings, under Security click on Code security and analysis.
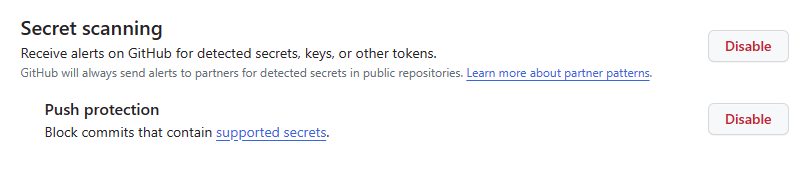
From the GitHub docs, “Push protection prevents you from pushing secrets to your repository. When you enable push protection, GitHub scans your commits for secrets and prevents you from pushing them to your repository. If GitHub detects a secret in your commit, it will block the push and display an error message.”
So lets create a new branch and add the secret to the code and try to push it to the repository.
Please note, that there is only a limited set of secrets that GitHub will pick up. For a full list, check out the GitHub documentation here.
For this example, I tried to commit a Storage Account access key and connection string.

What I will say about the push protection is that it is not perfect, and having now had time to read into the documentation, the amount of secrets it could/should pick up is limited. Which is a real shame.
Conclusion
So there we are, the end the page already! What are the take aways from this post?
Well as Gandalf said, “Keep it Secret, Keep it Safe”. 🧙♂️
Hopefully this gives you a good understanding of how to keep your secrets safe when working with Git and GitHub.