Blogging often serves a dual purpose: not only does it help others who may be facing similar challenges, but it also acts as a personal reference for when we inevitably forget the finer details of our own work. This post is a perfect example of that. While it’s written to assist anyone who might find themselves in need of the same information, it also serves as a handy reminder for me when I look back on it in the future. Hopefully, this can help others in the same way it helps me!
Community Note:
I’m hoping this will be a ‘living’ post that I can update over time whenever I come across things I need to remember, and later forget 😅
What is an Azure Function App
An Azure Function App is a serverless compute service in Microsoft Azure that allows you to run event-driven, lightweight code without having to manage the underlying infrastructure. It is designed to execute small pieces of code, called functions, in response to events such as HTTP requests, timer triggers, message queues, or changes in Azure resources.
Key Features
- Event-Driven & Serverless – Code runs only when triggered, and Azure automatically scales resources as needed.
- Multiple Triggers – Supports HTTP, Timer, Queue, Blob, Event Grid, Event Hub, Service Bus, and more.
- Multiple Programming Languages – Supports C#, JavaScript (Node.js), Python, PowerShell, Java, and TypeScript.
- Automatic Scaling – Scales up/down dynamically based on demand.
- Flexible Hosting Options:
- Consumption Plan (pay-per-execution, fully serverless)
- Premium Plan (scales automatically but provides always-on instances)
- Dedicated (App Service) Plan (fixed infrastructure, good for long-running functions)
- Integration with Azure Services – Works with Storage, SQL, Cosmos DB, Azure Monitor, and more.
- Durable Functions – Enables stateful, long-running workflows.
Use Cases
- Automation & Scheduling (e.g., clean-up tasks, report generation)
- Event Processing (e.g., handling messages from an Azure Queue)
- Webhooks & API Endpoints (e.g., processing HTTP requests)
- Data Transformation & Processing (e.g., transforming data before storing it)
- Security & Monitoring (e.g., responding to security alerts)
For more information, you can check out the MIcrosoft Learn Docs: Azure Function App
For Infrastructure As Code things, You can check out the Azure Verified Modules Web/Function Apps
Configuration Notes and Tips
Requirements.psd1
When wanting to connect to Azure, The base module you need is Az.Accounts
If you’re wanting to interact with Microsoft Graph, you need Microsoft.Graph.Authentication
Key Considerations
Selective vs. Wildcard (‘Az.’ & ‘Microsoft.Graph.’) Loading
- Using
Az.*andMicrosoft.Graph.*loads all submodules under the respective parent modules. - This provides maximum functionality but significantly increases the cold start time for an Azure Function because all modules are installed and loaded, even if not used.
Cold Start Performance Impact
- Loading only necessary modules (
Az.Accounts,Microsoft.Graph.Authentication) improves start time. - Loading all modules (
Az.*,Microsoft.Graph.*) increases size and loading time, potentially leading to performance issues.
Recommended Approach
- If you only need authentication, load
Az.AccountsandMicrosoft.Graph.Authentication. - If you need full functionality, you may use wildcards but should be aware of the impact on load times.
Basic Authentication Modules
| |
All Modules
| |
Azure Authentication
To Configure Azure Authentication, First you need to create an environment variable for managedIdentityId, This needs to be the Client Id
IMPORTANT
Don’t forget to assign the User Managed Identity RBAC Permissions to the Subscription
| |
Configuring CORS Access
Cross-Origin Resource Sharing (CORS) is a security feature implemented by web browsers to control how resources on a web server can be accessed from different origins (i.e., domain, protocol, or port). It ensures that resources on a web server are only accessible by web pages from allowed origins, which helps prevent malicious websites from accessing sensitive data.
In a typical scenario, a browser-based JavaScript application might want to make an API call to a backend service (like an Azure Function). If the frontend and backend are hosted on different domains (cross-origin), the browser by default blocks the request for security reasons, unless the backend explicitly allows it.
Azure Portal Configuration
When you create an Azure Function, CORS is not configured out of the box, (When using click ops), If you try and run a function you’ll get this message:
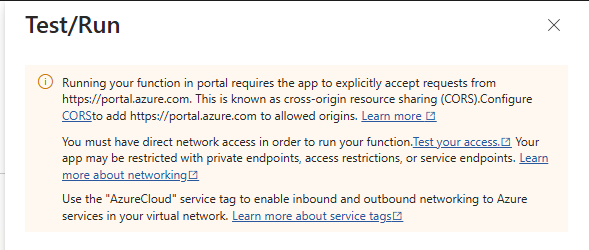
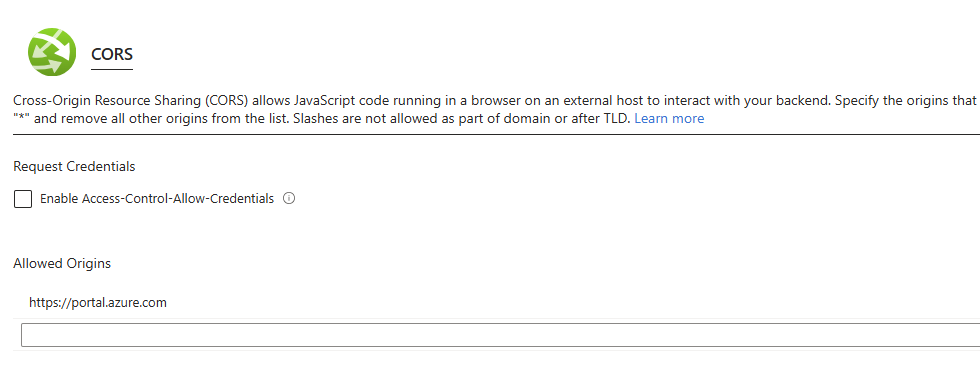
To resolve this, Head to API > CORS and add the url: https://portal.azure.com
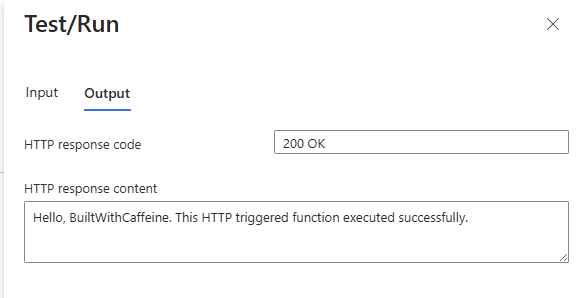
Once saved, head back to the function and try execute Try/Run, this time it will pass and give you the results you hoped for 🎉
Below is a snippet for the Bicep configuration
| |
Key Vault Values
Azure Key Vault is a centralized, secure service to manage secrets, keys, and certificates. When developing a Function App, securely storing sensitive data such as connection strings, API keys, and passwords is crucial. By using Azure Key Vault, you can ensure that secrets are stored in a secure and compliant manner, eliminating the need to store them in code or configuration files, which could lead to accidental exposure.
Key benefits of using Azure Key Vault include:
- Centralized Management: Manage secrets, keys, and certificates in one place.
- Access Control: Fine-grained access policies to restrict who can access which secrets.
- Auditability: Built-in logging and monitoring for security purposes.
- Security Best Practices: Azure Key Vault integrates with managed identities, providing seamless and secure access to secrets without needing to handle credentials in code.
Storage Account Setup
Using the Azure Verified Modules, We can use export the Access Keys and Connection Strings direct into an Azure Key Vault, Below is an example module which passed these values into the keyvault
| |
Using Azure Key Vault References in Application Settings
You can configure your Function App’s settings to pull secrets directly from Azure Key Vault. By using a Key Vault reference, you can inject secrets into your function’s environment without storing them explicitly in the configuration.
| |
In this case, ${keyvaultName} is replaced by the name of your Key Vault, and connectionString1 is the name of the secret. When the Function App starts, Azure automatically resolves the secret and makes it available as an environment variable.
ZIP Deployments
Why Use WEBSITE_RUN_FROM_PACKAGE?
WEBSITE_RUN_FROM_PACKAGE is an Azure App Service setting that allows you to deploy your application as a ZIP package rather than individual files. This method offers several benefits:
Faster and More Reliable Deployments
By deploying a single package, you minimize file transfers, reducing deployment time and the risk of incomplete deployments.
Read-Only File System for Consistency
Setting WEBSITE_RUN_FROM_PACKAGE=1 mounts the package as a read-only file system, preventing unintended modifications and ensuring consistency across deployments.
Seamless CI/CD Integration
It works well with CI/CD pipelines like Azure DevOps and GitHub Actions, enabling streamlined, automated deployments.
Reduced Cold Start Time
Preloading the package as a read-only mount can improve startup performance, especially for larger applications.
Easy Rollbacks
Since deployments are immutable, rolling back is as simple as redeploying a previous ZIP package.
Ideal for Azure Functions and App Services
For Azure Functions, this method enhances performance, reduces deployment time, and ensures a stable execution environment.
Building Function Zip
Prepare Your ZIP Package
Ensure your application files are structured correctly. For an Azure Function App, the expected format is:
| |
Upload the Zip File to a Storage Account, Or Repository
Configure with Bicep
If using Infrastructure as Code, add this setting under appSettingsKeyValuePairs:
| |
Auto Update
Auto-Update Scenarios
Auto-updating behavior depends on where the package is stored:
Deployment via Zip in Azure Storage (Recommended for Auto-Updates)
- If
WEBSITE_RUN_FROM_PACKAGEpoints to an Azure Blob Storage URL (e.g.,https://storageaccount.blob.core.windows.net/...), the app will always run from the latest version of that blob. - When you replace the zip package in storage, the next restart (manual or automatic) picks up the new package.
- This allows for automatic updates without redeploying the app.
Deployment via Zip Push to Kudu (Azure App Service Zip Deploy)
- If you deploy a zip package using
az webapp deployment source config-zip, it is copied toD:\home\data\SitePackages. - The app does not auto-update unless a new zip package is deployed.
- Restarting the app does not fetch a new version unless a fresh deployment occurs.
Deployment via CI/CD (Azure DevOps, GitHub Actions, etc.)
- CI/CD pipelines can push a new zip package automatically when changes are made.
- The app updates whenever a new package is deployed via the pipeline.
How to Ensure Auto-Updates
Use Azure Storage URL (WEBSITE_RUN_FROM_PACKAGE=<Blob URL>)
- Upload a new zip file to the storage account.
- Restart the app (
az webapp restartor via the portal) to apply the update.
Enable Continuous Deployment (CI/CD)
- Automate package deployment using Azure DevOps, GitHub Actions, or similar tools.
Set Up App Restart Mechanisms
- Use deployment slots to swap updated versions seamlessly.
- Schedule periodic restarts via Azure Functions Timer Trigger or Logic Apps.