In today’s ever-evolving cybersecurity landscape, ensuring the integrity and authenticity of your domain name system (DNS) records is more important than ever. DNS Security Extensions (DNSSEC) help defend against attacks such as DNS spoofing or man-in-the-middle attacks by securing DNS data. With Azure DNSSEC, you can cryptographically sign your DNS records, ensuring their authenticity and protecting them from tampering.
In this blog post, we’ll dive into what Azure DNSSEC is, how it works, and how you can easily enable it for your Azure-hosted domains.
What is Azure DNSSEC?
DNSSEC is a security protocol that adds a layer of cryptographic protection to DNS records. It ensures that DNS responses are authentic and haven’t been altered during transmission, making it harder for attackers to spoof DNS records.
Azure DNSSEC is Microsoft’s solution for enabling DNSSEC on Azure DNS zones. With this service, you get automated key management, seamless integration with Azure DNS, and support for both signing and validating DNS records, all of which help you secure your DNS infrastructure.
Key Features of Azure DNSSEC
Automated Key Management Azure DNSSEC automates the generation and management of cryptographic keys, removing the complexity of manual key rotation and renewal.
Chain of Trust DNSSEC establishes a chain of trust, ensuring that DNS responses are validated by a trusted, hierarchical model. This chain helps confirm that the data you receive from DNS resolvers is valid and untampered.
Protection Against DNS Spoofing By signing DNS records with cryptographic keys, DNSSEC prevents attackers from falsifying DNS responses, protecting users from malicious redirection and man-in-the-middle attacks.
Seamless Azure DNS Integration Azure DNSSEC works effortlessly with your existing Azure DNS zones, providing a native solution that’s easy to configure and manage through the Azure portal.
How Does Azure DNSSEC Work?
DNSSEC operates by signing DNS records using public-key cryptography. When a DNS resolver queries a DNSSEC-enabled domain, it checks the signatures of the DNS response to ensure it hasn’t been altered in transit.
The DNSSEC Process
Key Signing Key (KSK) and Zone Signing Key (ZSK): Azure DNSSEC automatically generates and manages two types of cryptographic keys: the KSK (used to sign the DNS zone’s ZSK) and the ZSK (used to sign the DNS records in the zone). Azure ensures that these keys are rotated and managed securely.
Signing the DNS Zone: Once the keys are generated, the DNS records in the Azure DNS zone are signed using the ZSK, creating a digital signature for each record.
Publishing DS Records: To complete the trust chain, the Delegation Signer (DS) record is published to your domain registrar. This establishes a link between your domain’s DNS records and the DNSSEC-enabled chain of trust.
Validation by DNS Resolvers: When a client queries a DNSSEC-enabled domain, the resolver checks the authenticity of the response by validating the signature against the published keys. If the signature is valid, the resolver knows the response hasn’t been tampered with.
Enable DNSSEC - Primary Zone
Enabling DNSSEC for an Azure DNS zone is straightforward and can be done through the Azure portal, Azure CLI, or Azure PowerShell.
Using Azure Portal
Official Docs: DNSSec How to - ‘Portal’
Navigate to Azure DNS Zones in the Azure portal, Select the DNS zone you want to enable DNSSEC for.
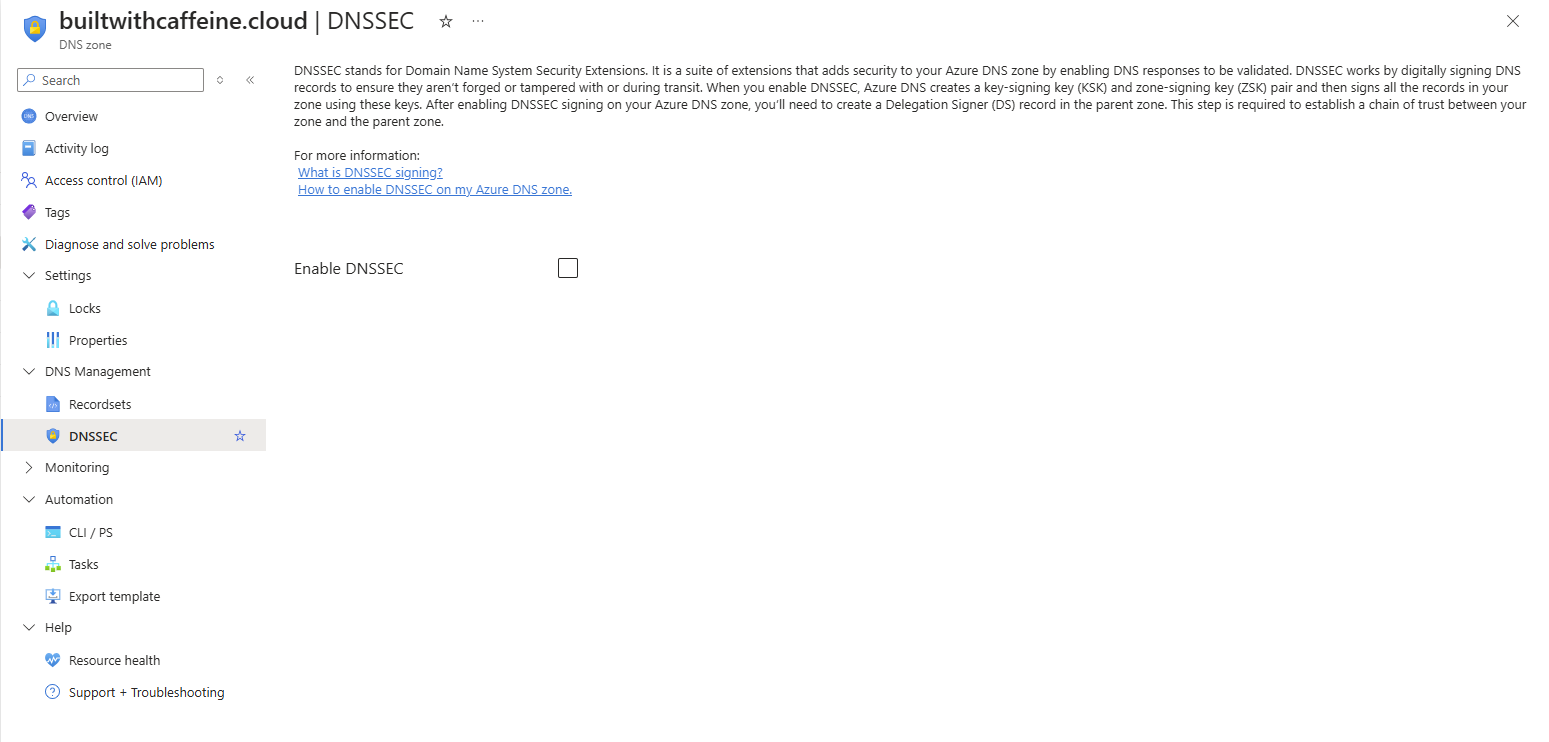
Click on DNSSEC, then select Enable DNSSEC.
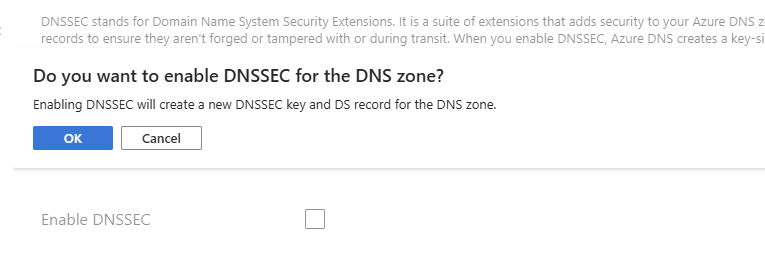
Azure will automatically generate and manage the keys and signatures.

Copy the Delegation Signer (DS) record and configure it at your domain registrar.
For me, I’m using 123-Reg for my Register.
‘Domain Portfolio’ > ‘builtwithcaffine.cloud’ > ‘DNS’ > ‘DS Records’

Once added, we can check using the DNSSEC Debugging Tool: https://dnssec-debugger.verisignlabs.com/
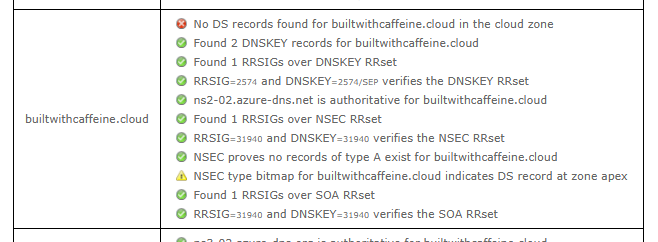
DNS propagation can take time as changes gradually spread across DNS servers worldwide. Depending on TTL settings and caching, updates might not be instantly visible. So while the internet catches up, you might as well enjoy a well-earned break!
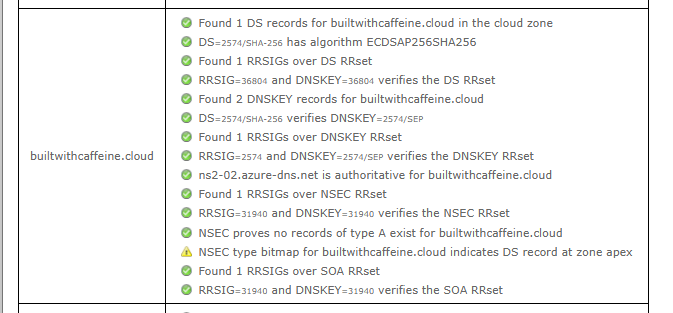
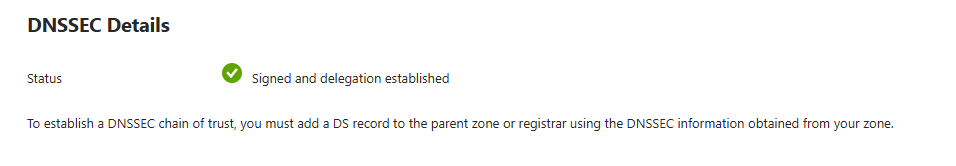
Finally checking in the Azure Portal, all is now green and healthy! 🎉
Using Azure CLI
Official Docs: DNSSec How to - ‘Azure CLI’
Please note, this will just enable the DNSSEC Configuration on the Public DNS Zone, You’ll still need to head to your registrar and add the DS Configuration.
Create Azure Public DNS Zone
| |
Enable DNSSEC on Public DNS Zone
| |
Using Azure PowerShell
Official Docs: DNSSec How to - ‘PowerShell’
You’ll need Az.DNS installed for the Set-AzDNSZone command.
Create Azure Public DNS Zone
| |
Enable DNSSEC on Public DNS Zone
| |
Once enabled, your DNS records will be cryptographically signed, ensuring security and integrity.
Enabling DNSSEC for a Child Zone
When using a child DNS zone in Azure, enabling DNSSEC on the child zone requires you to create a ‘DS’ (Delegation Signer) record in the parent (primary) zone.
For example, in the case of the playground zone az.builtwithcaffeine.cloud.

Once enabled, we need to create a ‘DS’ record in the primary zone ‘builtwithcaffeine.cloud’

When adding the record, the prefix is the child zone name az

Let DNS propagation do its thing and grab some caffeine! and that is it! 🎉

Considerations and Best Practices
| Best Practice | Description |
|---|---|
| Ensure DNSSEC Support at Your Registrar | Some domain registrars may not support DNSSEC. Ensure your provider supports DNSSEC before enabling it. |
| Monitor Expiry of DNSSEC Keys | Although Azure manages key rotation, it’s important to monitor DNSSEC status to avoid expired signatures causing issues. |
| Test DNSSEC Validation | Use online tools like DNSViz or Verisign Labs DNSSEC Debugger to validate your DNSSEC setup. |
| Combine DNSSEC with Other Security Measures | DNSSEC protects DNS integrity, but it does not encrypt data. Consider using TLS and other security measures to further protect your domain. |
Wrap Up
Azure DNSSEC is an essential security feature that helps protect your DNS records from attacks and tampering. By enabling DNSSEC, you add a layer of trust and authenticity to your domains, preventing common DNS-based attacks. With Azure’s automated key management and seamless integration, securing your domains with DNSSEC is easier than ever.
If you’re managing DNS in Azure, enabling DNSSEC should be a top priority to safeguard your online presence.