Today I Learned…
Every day offers a chance to learn something new, and today was no exception. This post dives into a real-world issue I encountered with a customer, which also turned out to be a valuable learning experience for me. Let’s dive into the details.
The Scenario
Picture this setup:
- Private Link Service
- Load Balancer
- Virtual Machine
The customer could access the services hosted on the virtual machine, but the VM itself had no outbound internet access.
If you’re already familiar with Azure networking quirks, you might guess where this story is heading. But for me, this was a new discovery, and it took some troubleshooting to figure it out. 😅
The Issue
During the investigation, I noticed something peculiar:
Running nslookup microsoft.com from the virtual machine worked perfectly, resolving the url. However, opening a browser and navigating to microsoft.com resulted in the dreaded:
Hmmm… can’t reach this page.
This revealed a gap in outbound internet connectivity—an essential aspect often overlooked in Azure networking setups.
Outbound Options
To resolve the issue, I explored several options based on Microsoft’s documentation: Azure Load Balancer - Outbound Connections.
Here’s a summary of the methods and their pros/cons:
| # | Method | Type of Port Allocation | Production-Grade? | Rating | Notes |
|---|---|---|---|---|---|
| 1 | Use the frontend IP address(es) of a load balancer for outbound via outbound rules | Static, explicit | Yes, but not at scale | OK | Limited scalability. Suitable for small-scale deployments. |
| 2 | Associate a NAT Gateway to the subnet | Dynamic, explicit | Yes | Best | Highly scalable and secure. Recommended by Microsoft for new deployments. |
| 3 | Assign a public IP to the virtual machine | Static, explicit | Yes | OK | Direct exposure of the VM, even with NSGs, is not ideal for production environments. |
| 4 | Default outbound access | Implicit | No | Worst | Insecure and unreliable. Deprecated for new deployments after September 2025. |
| 5 | User Defined Route (UDR) | Static, explicit | Yes | OK | Requires a Network Virtual Appliance (NVA). Provides flexibility but needs careful management. |
The Fixes
Default Outbound (Heads-Up 🚨)
While not a recommended fix, it’s worth noting that default outbound access is being retired in September 2025. If you’re using it, start planning to migrate to a supported solution.
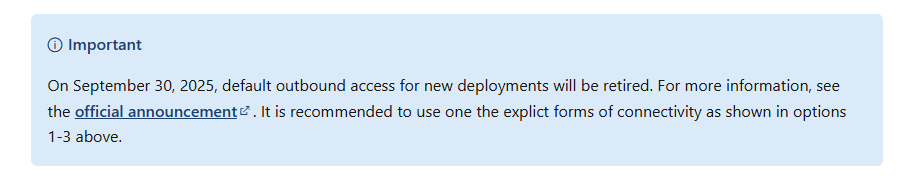
For more details, see the Azure Updates Article.
Public IP Address
Assigning a public IP to the virtual machine can restore outbound connectivity. However, exposing the VM directly to the internet—even with a Network Security Group (NSG)—is not a best practice.
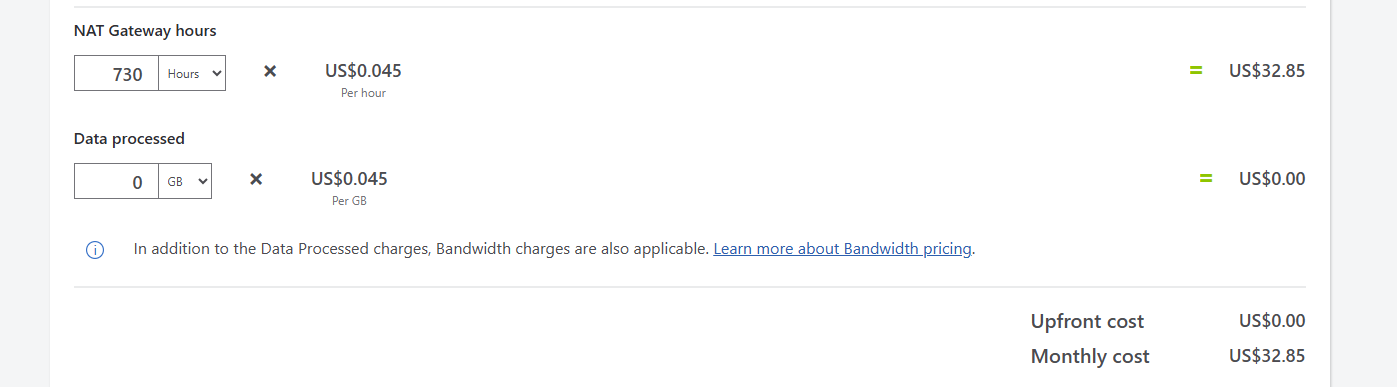
NAT Gateway (Recommended 🎯)
NAT Gateway is Microsoft’s recommended solution moving forward. Here’s what it offers:
Azure NAT Gateway is a fully managed and highly resilient Network Address Translation (NAT) service. It allows private subnets to connect outbound to the internet securely, while preventing unsolicited inbound connections.
If you’re unfamiliar with NAT Gateway, check the docs here: NAT Overview.
Key Highlights:
- Supports dynamic allocation of outbound ports.
- Ensures outbound traffic remains private and secure.
- Comes with a cost, so plan accordingly.
User Defined Route (UDR)
A User Defined Route is another option, especially if you have a Network Virtual Appliance (NVA) (e.g., Sophos XG, Fortigate). It lets you control outbound routing while leveraging the NVA for advanced network functions.
Example Azure CLI Script:
# Variables
RESOURCE_GROUP="your-resource-group"
ROUTE_TABLE_NAME="your-route-table-name"
ROUTE_NAME="your-route-name"
DESTINATION_CIDR="0.0.0.0" # Replace with the destination CIDR block
NEXT_HOP_IP="10.1.0.4" # Replace with the NVA's IP address
LOCATION="westeurope" # Replace with your desired location
# Step 1: Create a route table
az network route-table create \
--resource-group $RESOURCE_GROUP \
--name $ROUTE_TABLE_NAME \
--location $LOCATION
# Step 2: Add a route to the route table
az network route-table route create \
--resource-group $RESOURCE_GROUP \
--route-table-name $ROUTE_TABLE_NAME \
--name $ROUTE_NAME \
--address-prefix $DESTINATION_CIDR \
--next-hop-type VirtualAppliance \
--next-hop-ip-address $NEXT_HOP_IP
Wrap Up
Outbound connectivity is a crucial yet often overlooked aspect of Azure networking. With solutions like NAT Gateway or UDRs, you can maintain secure and scalable outbound access while avoiding pitfalls like public IP exposure or relying on deprecated features.